How Can We Help?
Table of Contents
Risk management works by analyzing backup executions, both in terms of their characteristics, but also with the policies and associated incidents.
The items analyzed are:
- Volume (Increase/decrease greater than 50%);
- Execution Time (Increase/decrease greater than 50%);
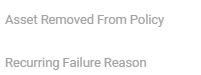
- Associated Policy (Host removal, disabling);
- Recurrent Failure (failure category) – The risk is generated based on incidents of the same policy and company that had the same category of failures at least 3 times in the 30-day period.
Risk Type
We can filter the types of Risks according to the type or other advanced characteristics.
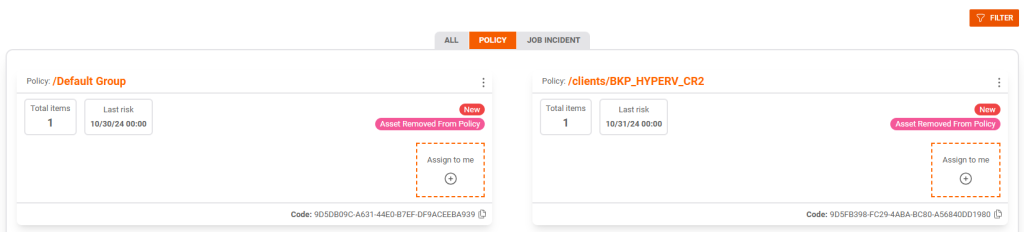
To interact with a risk, it must first be associated with a user.
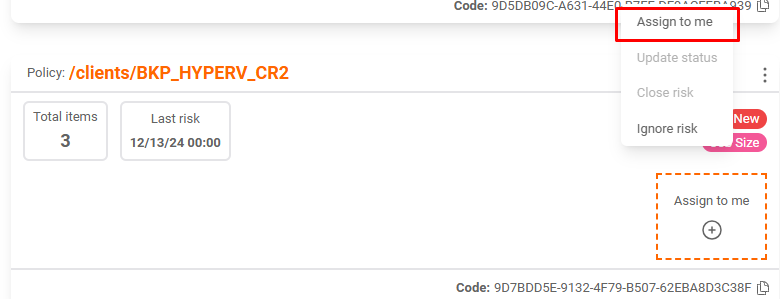
After the association, we can:
- Update Status: Where we place important information regarding the progress;
- Close: To place a closing solution;
- Ignore: Ignore this risk after analyzing that it is part of the normal behavior of the environment;
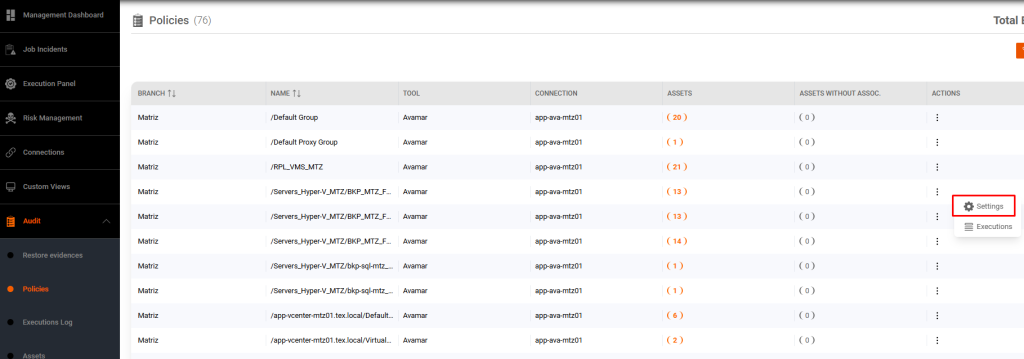
Risks are generated automatically by the FenixDFA system, but we can choose the policies that will be subject to this analysis.
Browsing in Audit, then in Policy, we have the list of all policies detected by FenixDFA.
In the action column, by clicking on settings, we can select the analyses that make sense in the context of each policy.
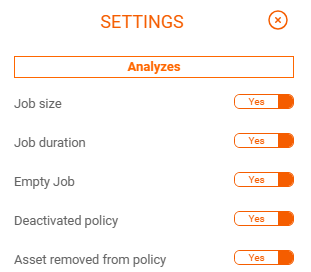
To check the completed risks, we have to go to filter and select show resolved